VLANs: Navigate your Network’s Security Armor

Safeguarding data and fortifying security are always top priorities. Virtual LANs (VLANs) are tools to improve network security, protecting organizations against potential threats.
Only managed switches and a few unmanaged switches can implement VLANs, empowering network administrators to elevate security measures significantly. VLANs are essential for network security in addition to implementing network segmentation for increased performance and scalability. Admins can isolate specific network segments so that only devices in the same VLAN can communicate with one another. This isolation restricts network-wide cyberattacks.
Moreover, VLANs support network separation, enhance access control, and tailor security policies, reducing the risk of unauthorized access while encouraging compliance and privacy efforts.
3 Ways VLANs Fortify Security
The vital role of VLANs in enhancing network protection gives network admins a comprehensive view of how to defend their systems.
- Customizes Access Authorizations
VLANs enable access controls by segmenting a network. Organizations can define access policies specific to each segment. For instance, confidential data can be placed in a separate VLAN, accessible only to authorized users. This level of control minimizes the risk of unauthorized access and data breaches. - Mitigates Security Risks
Sensitive data isolation makes it more difficult for an intruder to get lateral network access when a security breach occurs. Even if one segment has been compromised, the hacker’s access to other networks is restricted, reducing the scope of possible damage. - Enhances Layered Security
VLANs give an extra layer of defense to existing security measures. VLANs produce a thorough security approach when paired with firewalls, intrusion detection systems, and other security technologies. They guarantee that if one security measure is disregarded, another layer of defense will still be in place.
Configuring VLANs for enhanced security involves network segmentation, assigning devices to specific VLANs, and defining access policies. Through proper configuration and management, network admins can tailor VLANs to meet their organization's security requirements.
4 Easy VLAN Configuration Steps
Network segmentation is a fundamental step towards network separation by creating controlled access points within the network. The extent to which network segmentation affects network separation depends on the security requirements and specific measures implemented within each segment, with separation representing a more robust isolation level.
Follow the network segmentation steps below to improve performance and security for streamlined network management:
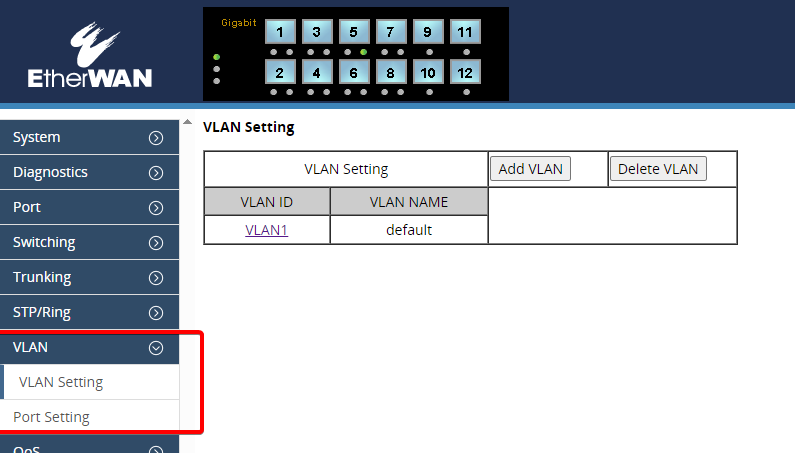
1. Establish or define the VLANs
Most switches offer a mechanism to define a list of configured VLANs, and to add them before configuring on any ports is essential.
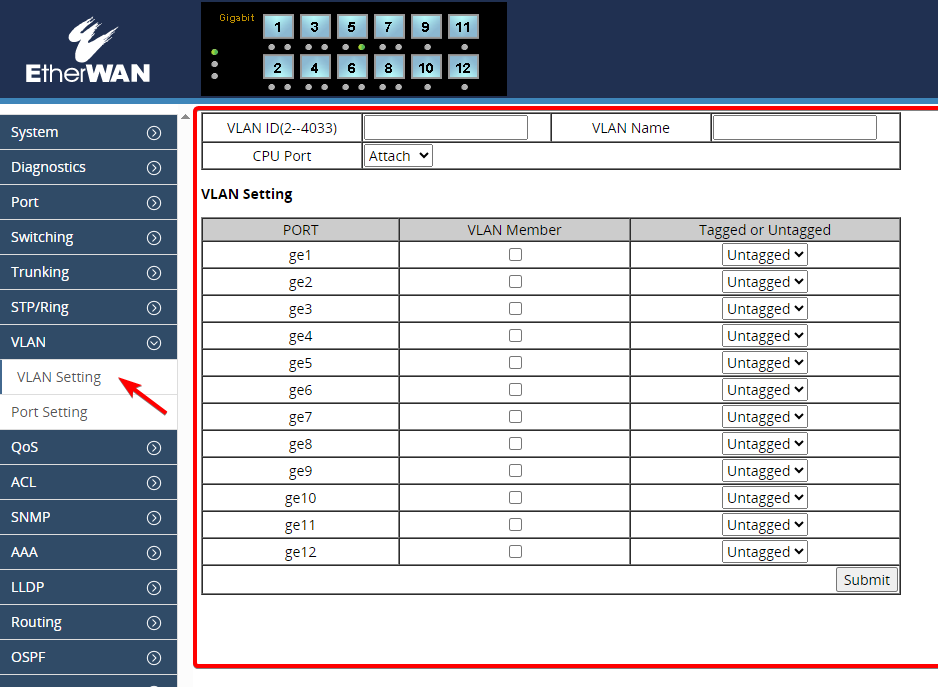
2. Set up the trunk ports
Configure the port to which the firewall is connected as a trunk port, ensuring it tags all possible VLANs on the interface.
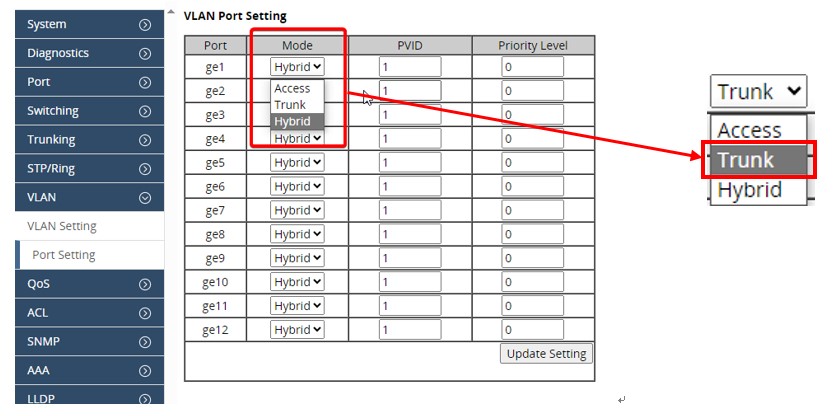
3. Configure the access ports
Set up ports for internal hosts as access ports on the desired VLANs, utilizing untagged VLANs for proper segmentation.
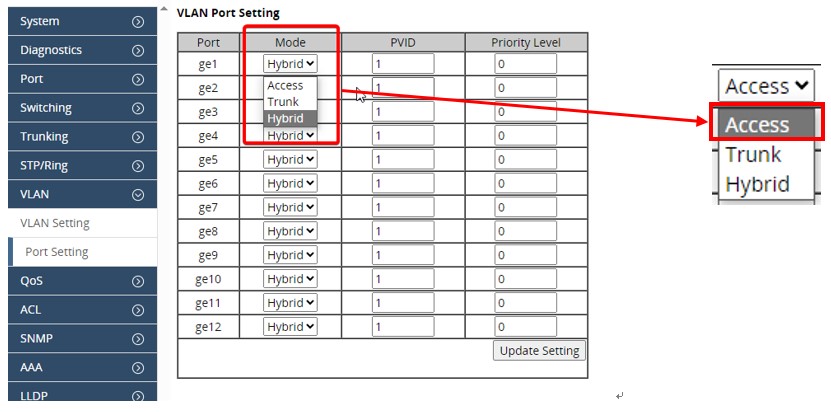
4. Set the port VLAN ID (PVID)
Some switches necessitate configuring the PVID for access ports, specifying the VLAN for traffic entering the switch port. This may be a one-step process, automatically tagging traffic, or for other switches, it might require configuration in one or two separate places.
VLANs in your Network Security Strategy
VLANs are a powerful ally in preserving data integrity and safeguarding network assets. Their contributions extend to improved performance, enhanced scalability, and fortified protection against threats. Through network segmentation, VLANs bolster isolation, mitigating the impact of potential cyberattacks. In tandem, network separation supports access control, reduces security risks, and supports compliance measures. In the evolving threat landscape, VLANs continue to prove indispensable for data protection and security within the framework of modern network infrastructure.
GET MORE DETAILSRead more
* Using VLAN Segmentation and Separation to Improve an ITS Network
* What is VLAN : A Brief Introduction to VLANs





